Windows Process Internals: A few Concepts to know before jumping on Memory Forensics [Part 4] — VADs
A Journey in to the Undocumented VAD Structures (Virtual Address Descriptors)
What is Virtual Address Descriptor (VAD)?
For each process, memory manager maintains a set of Virtual Address Descriptors (VADs) that describes the ranges of virtual memory address space reserved for that specific process. It also stores information about allocation type (private/shared), memory protection (read/write/execute etc.) and inheritance. VAD is a tree structure and like any tree structure it has a root (which is called Vadroot) and nodes/leafs (Vadnodes) that contains all the information related to memory ranges reserved for a specific process by the memory manager. For each chunk of a continuous virtual memory address allocations, memory manager creates a corresponding VAD node that contains the information about this continuous allocations and other information as mentioned above.
If any file is mapped in any of these memory regions, VAD node contains the full-path information for that file. This is really important information from the memory forensics perspective. If any dll or exe is mapped in one of these memory ranges then the VAD node (which is a Kernel structure) contains the full path on disk for that dll/exe. This information helps us in identifying any malicious activities like unlinking dll in the standard _PEB ldrmodules. The information is still available even if dll is unlinked from all 3 ldrmodules in _PEB (which is a user mode structure).
VAD information can be used in revealing many attacks like dll injection, reflective code injection etc. We will not talk about those attacks and how to identify them in this article as plenty of material available on the Internet for the same.
In this article, we will talk about the kernel data structures related to VAD in Win10. VAD structures have been undergone multiple changes during Windows transition from WinXP to Win10. We will talk about Win10 (build 18362.1016). There is not much information available about these structures available on the Internet. Many of VAD kernel structures are not documented properly.
Let us go through methodically and dig out the information about the mapped fie in a particular VADnode.
Which Volatility Plugins provide Information about VAD?
Vadinfo,vadtree and vaddump — we will not talk about these plugins here but we will talk about the kernel structures form which they fetch the information. I would like to show here the visual output(snapshot below)from the vadtree plugin — that is visually appealing and provides visual cues for quick analysis. We will talk about how to interpret this output in some other article.
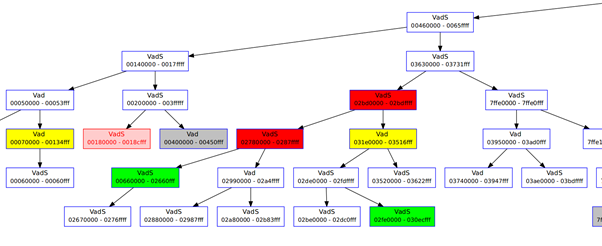
Let us Explore Kernel Memory Structures related to VAD
First of all, let us get hold of Vadroot. As mentioned above, each process has its vadtree, let us enumerate the process and pick any of the process randomly. Once we identify the process, we need to enumerate _EPROCESS to get the address of the Vadroot as Vadroot is one of the fields of _EPROCESS structure.
Let’s say, I have identified a random process and its _EPROCESS is at the memory address location ffffaf0f07a7e080. Let us enumerate the _EPROCESS and grep Vadroot.

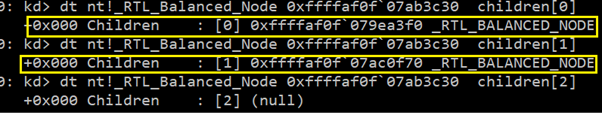
You can see that Vadroot is a _RTL_AVL_TREE structure and there is a pointer to the first node 0xffffaf0f`07ab3c30 of the tree. Now, as shown in the figure, the data structure at 0xffffaf0f`07ab3c30 is of RTL_BALANCED_NODE. If we enumerate that we will get the information about the its children and other related information to that node.

You can see here that there are fields like Children, Left and Right. There are 2 children of this node and there is a pointer to each child. One child would be in the left of this node and one child would be in right of this node based on its memory locations. If we further enumerates the Children we get the same information as Left and Right fields.
Each node has a its Tag value which comes before the actual structure starts in the memory location. The tag of the node will let you understand what kind of Information is stored in the memory ranges of that node.
Secondly, _RTL_BALANCED_NODE is alias for _MMVAD and _MMVAD_Short. These are the actual structures that we need to enumerate.
VAD Tags
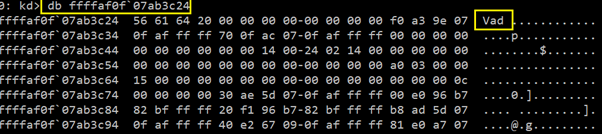
Let us enumerate the Tag for the first node and see what Tag it contains. Tag information is contained 12bytes before the actual node structure starts. So, we need to look at the 12 bytes before the structure. So, our first node is at 0xffffaf0f`07ab3c30.
Memory Mapped Files
You can see the Tag “Vad” which indicates that this node is of _MMVAD structure. So, let us enumerate this node to get the specific information about the name of the file that has been mapped in a specific section.
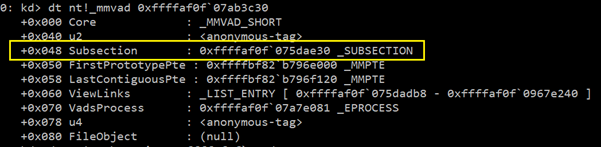
We need to focus on the fields “subsection” as this field contains the information about the mapped file in that region of the virtual memory. Let us enumerate it.
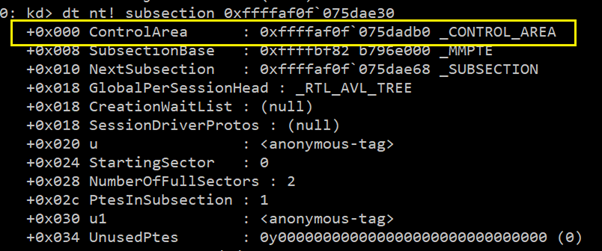
Focus on ControlArea here and enumerate it. You will get a FilePointer in this field.
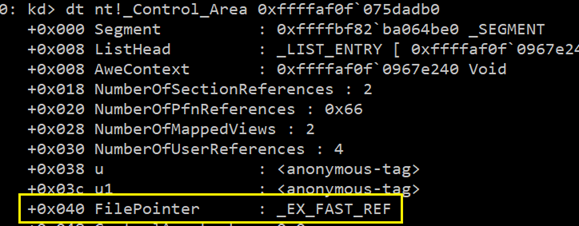
Now, the trickiest part comes now. This file pointer is not a straight forward pointer the _FILE_OBJECT. It is a _EX_FAST_REF structure and we need to do some jugglery to get the file object pointer from it. I would like to thank to the @ McDermott Cybersecurity, LLC’s blog. Without referring to this blog, it would have been impossible to get to the correct file pointer. Now, here is the magic. We need to replace the last bit of the FilePointer field in the previous output to 0(Zero) and that would be our pointer to the _FILE_OBJECT. So, we have a filepointer at 0xffffaf0f`078d237b.

Replacing last bit of this address with zero will give us 0xffffaf0f`078d2370. Enumerate file_object at this pointer.
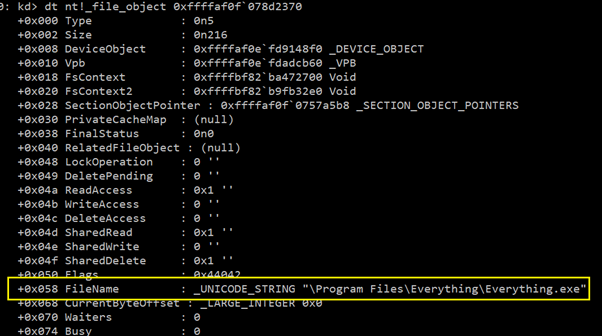
You can see that we have got the file name here. It shows that everything.exe is mapped in the ranges described by this node and the full path to the binary is “\Program Files\Everything\Everything.exe”.
VAD Flags
We can talk about the Flags as well. There are multiple Flags associated with every node. However, we will talk about only memory protection flag as it is one of the important flags for any node.

Please refer above table to understand the Protection type corresponding to the Protection Flags Value. Let us examine, protection flag value for the node.
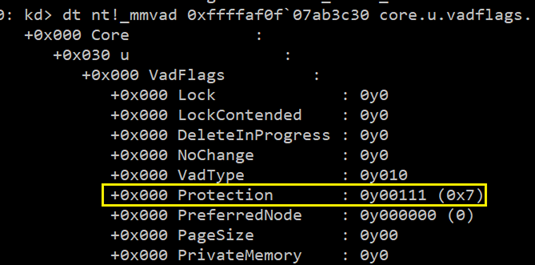
The value of the Protection flag is 0x7 which means the protection is EXECUTE_WRITECOPY. This is the typical memory protection used for the memory ranges where exe/dll (binary) files are mapped.

If you have observed “VadType” the previous output (right above the “Protection”)then it is 2 which is equivalent to VadImageMap. That means that there is an image mapped in the regions of the Vadnode.
There are many things to explore in each and every vad kernel structures. We have covered here a few important structures and associated key fields.
That’s it for now, folks!! Happy hunting, fellas!!
by :
Kirtar Oza
Twitter : Krishna (@kirtar_oza)
LinkedIn: https://www.linkedin.com/in/kirtaroza/
email: kirtar.oza@gmail.com
References
http://mcdermottcybersecurity.com/articles/x64-kernel-privilege-escalation
http://www.ivanlef0u.tuxfamily.org/?p=39
https://www.vergiliusproject.com/
